Today’s electronics are increasingly power-constrained. This is the case both for high-performance computing, where our ability to move to exascale computing is limited by the power consumption of supercomputers, and for relatively low-performance applications in IoT, where we wish to increase battery lifetimes.
The increasing demand to collect and analyze large volumes of data has led to an explosion of energy consumption in data centers, which is increasing exponentially over time.
As both active and passive power consumption rates scale with supply voltage (VDD), reducing the supply voltage is the main lever to decrease passive and dynamic power consumption. Voltage scaling in advanced technology nodes has not been able to keep up with dimensional scaling, and the scaling of operating voltages beyond 0.5 V poses a problem to MOSFETs.
“In 2050, the energy consumption of data centers worldwide is predicted to amount to three times the electric power generated in Japan by 2010.”
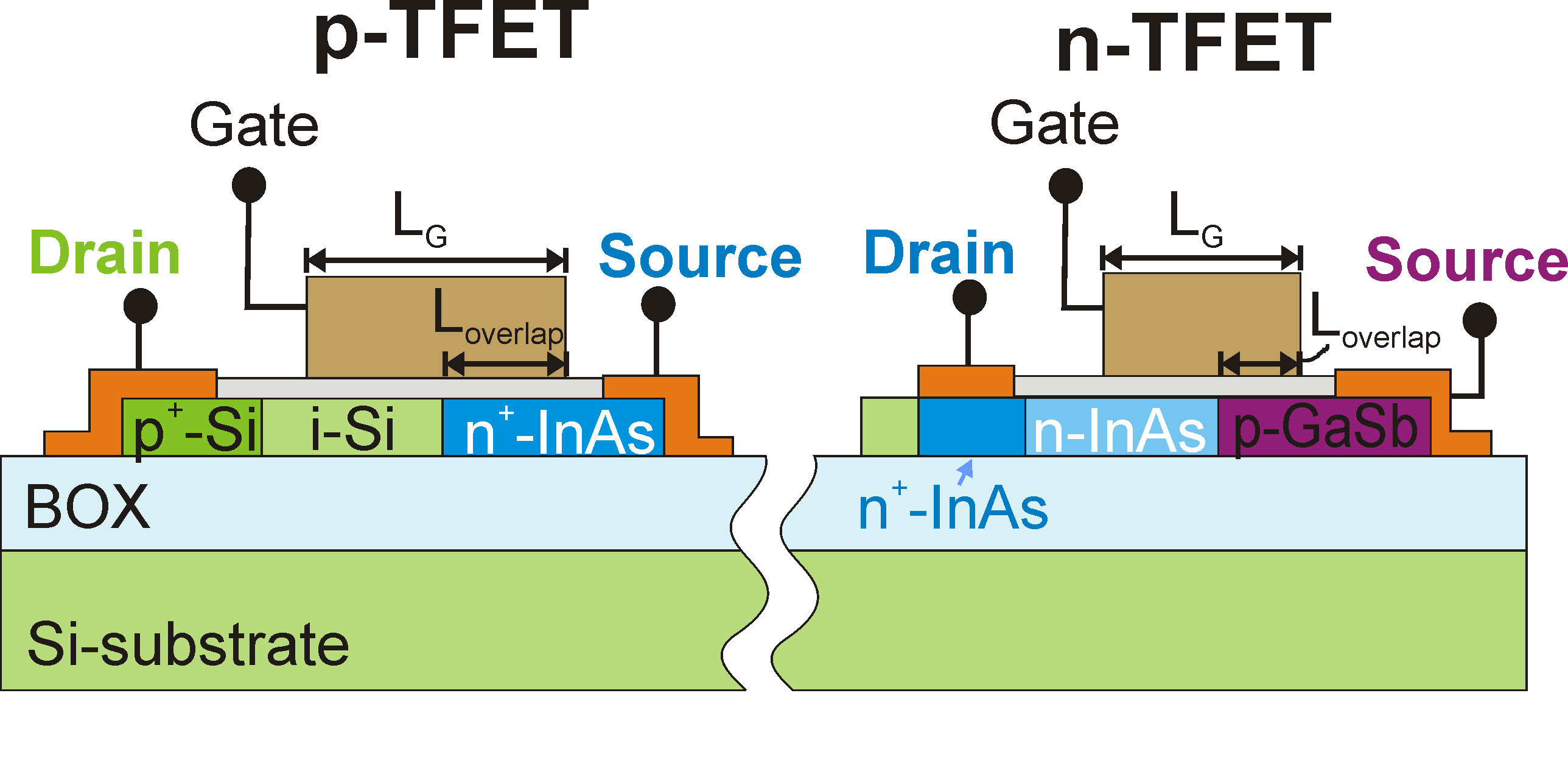
Researchers from the National Institute of Advanced Industrial Science and Technology (AIST) have demonstrated the operation of a synthetic electric field tunnel field-effect transistor with a new. E2SWITCH focuses on Tunnel FET (TFETs) as most promising energy efficient device candidates able to reduce the voltage supply of integrated circuits (.

—Compiled by TDK, based on the GPC Survey and estimation committee report 2008.
The inverse subthreshold slope (SS) in an ideal MOSFET is limited by the thermionic emission of electrons over a potential barrier, which has an intrinsic physical limit of
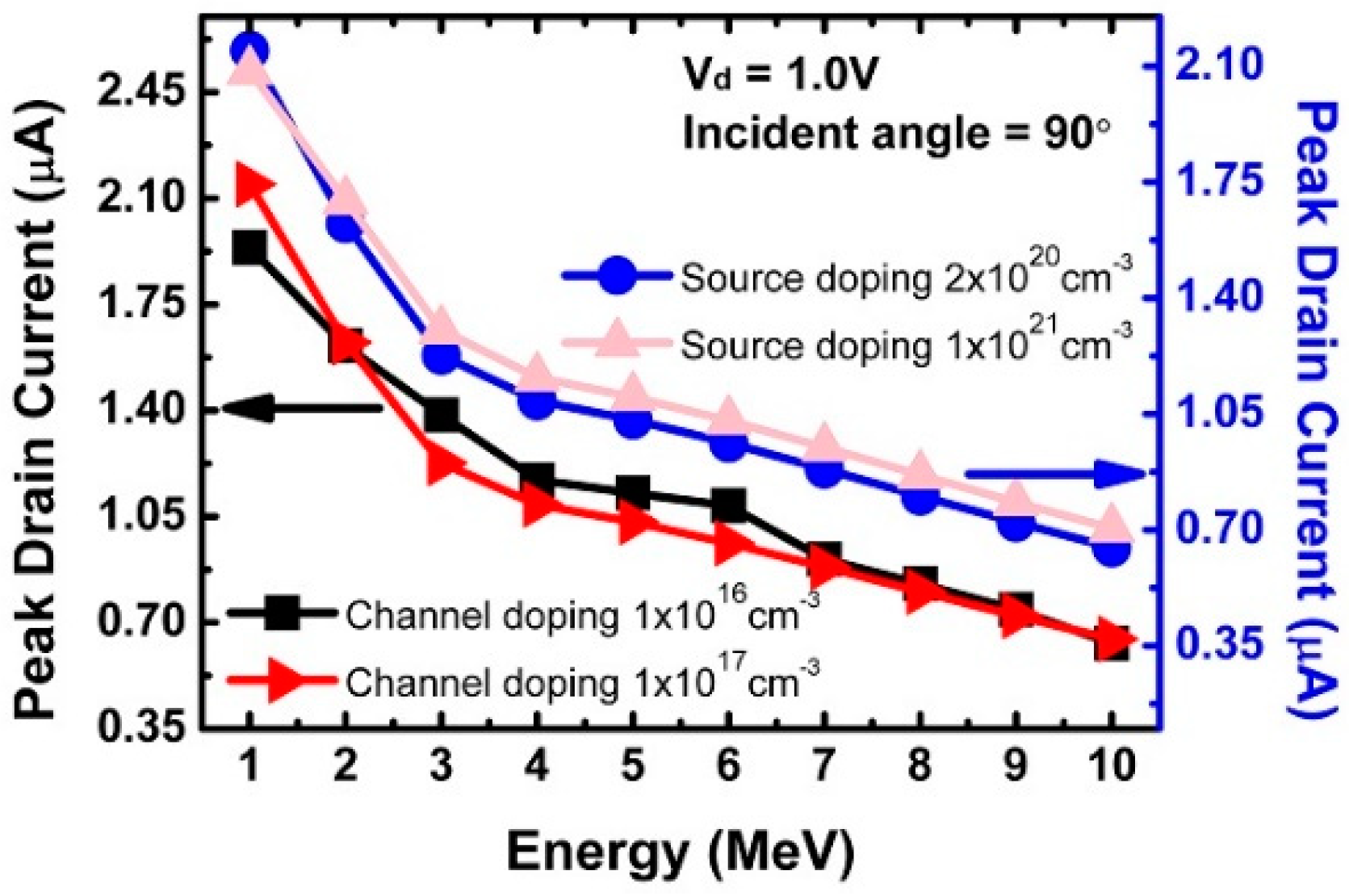
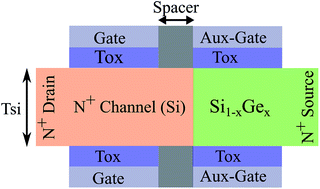
- Switching devices, such as the FB-FET 8, tunneling FET (TFET) 14 and impact ionization MOS (IMOS) 15, the Z2-FET shows superior switching performance under reasonably low V DD = 1.5 V supply voltage, see Fig. Operating principle The Z2-FET device operation can be.
- Tunnel field-effect transistor. Quite the same Wikipedia.
- This tutorial is for beginners in the field of microcontroller.In this case the microcontroller is AT89C51, a reprogrammable derivative of 8051. This purpose of this tutorial is to familiarize with the use of push button switch with the microcontroller.
where kB is Boltzmann’s constant, T is the temperature, q the elementary charge, Cd the depletion layer capacitance and Cox the gate-oxide capacitance. At 300 K, this results in an ideal value of 59.5 mV/dec, which is usually referred to as the 60 mV/dec limit of the MOSFET. Hence, there is a fundamental limit of how steep the turn-on of the MOSFET can be, independent of device design or charge carrier mobility in the material.
At higher bias levels, tunneling is less efficient than current mechanisms compared to drift diffusion in a MOSFET, but at voltage levels below 0.5 V it is hoped that tunnel FET might provide steep subthreshold swing combined with a higher current than in a comparable MOSFET.
Some Things You Wanted To Know About EPROMs,
But Didn't Know Whom Or What To Ask
by Dr Ah Clem Memory
I have been asked many times by users of the pocketprogrammer, if there is a good book that explains all the dirtylittle secrets about how EPROMs work. Well, it looks as if there isn'tone. So, here is my humble attempt to provide a dose of informationabout them.
If you think this information contains any errors, I would be gladto hear about it; (email inform@xtronics.com).This article is written with the philosophy that there is no such thingas a stupid question; only stupid mistakes from not asking stupidquestions. Things only seem complicated until you figure out how theywork, so lets dig in. (If you are familiar with binary, bits, bytes,hexadecimal, and ASCII you might want to skip the first section.)
What Is All This bits, bytes, Hexadecimal, Word, And ASCII StuffAbout?
Binary refers to base two or a two-state digitcalled a bit. A bit is either on or off - representedas a '1' for on (the set state) and '0' for off(the cleared state). Eight bits together form a byteand are written as 00110101b (or sometimes %00110101). The 'b'stands for binary, and lets you know that we aren't talkingabout 110,101, the decimal number. A byte or multiples of bytes set theregister size for microcomputers. Hexadecimal (hex) is abase 16 way of representing one byte. Hexadecimal usesthe digits 0,1,2,3,4,5,6,7,8,9,A, B, C, D, E, F. A byte requires just 2hex digits. Thus, FFh is a two hex digit representation of abyte. FFh is the same as 11111111b (the little 'h' designates ahexadecimal value sometimes a preceding '$' is used as in $FF)
A word usually refers to two bytes or 16 bits and can alsorefer to a 32 bit or wide word. We are fast approaching thetime when 64 bit words or doublewide words will becommon.
ASCII, is a code that represents the letters and numbers you cantype on a computer keyboard. Each letter you press is represented by aunique set of 8 bits or one byte.
EPROM Size Rating
EPROMs are rated in k-bits where k is equal to 1,024and the EPROM number generally (but not always) reflects the size. Butwhen we talk about memory size, we speak in terms of k-bytes.To change bits to bytes, simply divide the number of bits by 8 to getbytes.
A couple of examples will clear things up:
The 2716 EPROM number ends in 16 and thus is 16 k-bits in size or 16* 1,024 or 16,384 bits. Now, 16,384 bits divided by 8 gives us 2,048bytes or 2 k-bytes. Thus a 2716 is a 16 k-bit EPROM, but is most oftenexpressed as being 2 k-bytes in size.
Some EPROMs are word wide or 16 bits (2 bytes) wide. These EPROMsare also rated in bits, such as 27C1024 ; a 1 M-bit (Mega-bit),1,024 k-bits, 128 k-bytes, or 64 k-word EPROM. Such EPROMs come in 40pin packages to allow for the extra pins needed.
What is a Rom?
ROM stands for Read Only Memory. Theyare programmed at the factory at the time of manufacture with a specialmask, thus called a masked ROM. This is the cheapest way tomanufacture ROMs once you need more than 10,000 at a time. The drawbackis, if there is even one little bug in the software, that pile of10,000 ROMs becomes worthless. Be aware that some masked ROMs areunreadable by EPROM programmers
What is a PROM?
PROMs (Programmable Read Only Memory)consist of an array of fuses and thus can only be programmed one-time.Programming is accomplished with a current (instead of a voltage as areEPROMs) and requires a different type of programmer.
What is an EPROM?
EPROM(Erasable Programmable Read OnlyMemory) can be programmed and erased enabling them to bere-used. Erasure is accomplished using an UV (Ultra Violet) lightsource that shines through a quartz erasingwindow inthe EPROM package.
There also are OTP (One Time Programmable)EPROMs, sometimes called OTPROMs (One Time ProgrammableRead Only Memory), that are identical to anerasable EPROM, but lack an erasing window to reduce costs. To reducethe cost, these EPROMs come in a windowless plastic carrier,which is cheaper than the costly ceramic package required forthe erasing window. They can be programmed one time only, so these areused after the code is bug free.
What is an EEPROM?
An EEPROM (Electrically Erasable ProgrammableRead Only Memory) is similar to an EPROM but theerasure is accomplished using an electric field instead of anUV light source. This eliminates the need of a window. Usually, EEPROMrefers to a device that requires a programmer or special voltage toprogram it.
What is a Flash EPROM?
A flash EPROM is similar to an EEPROM except that flashEPROMs are erased all at once while a regular EEPROMs can erase onebyte at a time. In- circuit writing and erasing is possiblebecause no special voltages are required. To accomplish in-circuitoperation, you have to write special application software routines.Flash EPROMs are also called nonvolatile memory..
OK, So tell me, just how does an EPROM work?
EPROM memory cells use floating gate technology. A floatinggate is a gate with a special capacitor for its only electricalconnection. This special capacitor takes on an electrical charge in aquantum physics effect called tunneling. The presence of acharge determines the value (1 or 0) of the memory cell. In ourexample below, a room with a very narrow door represents the memorycell. People in the room represent electrons with their associatedcharge. These people can only enter or exit through a much too narrowdoor with much pushing or shoving to represent the tunneling effect.
Think of a room with about 30 people acting as the electron charge.A full room of people represents a '1'; when empty a zero. When anEPROM is erased, all 30 people are pushed into the room and provide thecharge that we call '1'. When we program an EPROM bit, we shove thesepeople until they pop back out by applying a pulse of high voltage tothe memory cell. This pulse drives the people out of the roomchanging the bit from a '1' to a '0'.
When programming a bit we can only change a 1 to a 0 becausechanging a 0 to a 1 requires erasing. To erase an EPROM, we apply an UV(Ultra-Violet) light (that shines directly on the chip) to drive ourimaginary people back into the room. Erasure works on the whole EPROMnot individual bits.
An EPROM cell is really an analog device. If it weredigital, we would only have an empty room or a room with one person init. Instead, a cell sensor circuitry compares how many peopleare in the room to a reference to determine if the cell represents a 1or 0. With more than 15 people in the room, the cell is considered a 1.
When programming an EPROM you have to apply the specifiedprogramming voltage for the specified time. Too short a time or too lowa voltage and not all the people get shoved out of the room. When youdon't program an EPROM properly and you still have 5 people in theroom, it will slow down the cell sensor circuitry, which slowsdown the read access time of the EPROM or might even corruptthe data. A similar thing can happen if you don't erase the EPROM longenough.
On the other hand, if you apply too high of a program voltage orover erase the EPROM, it is equivalent to blowing the doorframe rightout of the wall! Our imaginary people now enter and exit the room,milling around on their own whims and we no longer have informationstorage! The long and short of it is you need to double check Vppprogramming voltages and follow the recommended time for erasing (don'tstore unused chips in the eraser!). More about this later under theheading: erasing an EPROM.
(A little off the topic here, you may have seen little solid staterecording devices, sometimes used in answering machines, that recordvoice grade audio. The trick to getting so much audio into storage isby storing analog values into EEPROM cells! The recorded cells haveintermediate values that are not compared when read but out put as avoltage. When the memory cells are played back in consecutive order,the continuously changing values form an audio signal!)
A typical EPROM Pin Out
In single voltage EPROMs two of the pins are power pins; one is +5V andthe other ground. Single voltage EPROMs only require +5 to read them,but when programming they require a second voltage (Vpp). The oldthree-supply EPROMs require +5, +12 & -5Vdc just to read them. Yeta fourth voltage is required to program them! You no longer see threesupply EPROMs in new products, but they are still out there in olderequipment and are somewhat available for replacements. A good exampleis the three supply 2716 made by Texas Instruments, TI never made a2716 single supply. There are also EPROMs that are pin compatible butdo not have the same number such as the 2716 and the 2516 (T.I.'sversion of a single supply 2716). But for those of you who program alot of 2716's remember that T.I.'s 2716 are not the same as othermanufactures.
Back to pins, we look at the OE (Output Enable) and CE (ChipEnable). The CE pin enables and disables the data output. When disabledmost of the chip is in a low power sleep mode. The access timeof a chip is given from the time CE becomes active until data appears.
The access time using the OE pin is a lot shorter than CE becausethe OE pin disables only the data output pins, but not the rest of thechip. This allows data to be accessed at a much higher speed at thecost of increased power consumption.
When programming, we use the Vpp line to supply the programmingvoltage to the EPROM. Other times, Vpp is kept at +5.
Most EPROMs have 8 data lines (bits D0 - D7) forming a bytewide data bus, some have 16 data lines (bits D0 - D15)which makes it a word wide data bus. Enabling both CE and OEcauses all the bits to appear on the data lines; you can not enableindividual bits. The data of the byte or word, appears on these linesas 0's (about .4 Volts) or 1's (about 4 Volts). The data lines of anEPROM are bi-directional; they are outputs when you are reading theEPROM and inputs when you are programming it.
The address lines form an address bus made of inputsthat together select which location you want to read or program.Address lines start at A0 the LS (least significant) going up (A1, A2,A3...) with the address space doubling in size with each additionalpin.
Next, we have to consider the ROM compatible EPROM's. These have twopins, OE and A16, that are switched around. 1Mega-bit Mask ROMs are in28 pin packages and 1Mega-bit EPROMs are in 32 pin packages. Byswitching the two pins around, we can use a EPROM for testing anddeveloping purposes. Once the code is completely debugged and you areready to switch to masked ROMs, there is no reason to change the boardlayout. Simply put the EPROM in two pins lower in the socket (plug pin1 into pin3, pin 2 into pin4 . etc.). Companies that make video gamesand Laser printers use ROM compatible EPROM's in great quantities. Partnumbers to look for are 27100, 271000 & 27301. Remember, they are notpin compatible with 271001 or 27010.
Programming an EPROM
All EPROM bits are set to a 1 when erased (each byte = FFh). Whenprogramming an EPROM you can only change the 1s to 0s or clear bits. Ifyou program a byte to 10100101 (A5h), only the 0s locations changestate. Once a bit is changed to 0, you can't change it back to a 1without erasing the whole EPROM. We can go back and change any of the1s to 0s in a second programming session called patching. For example,the A5h byte (10100101) can be changed to 21h (00100001) but it can notbe changed to F5h (11110101). Once more, remember programming clearsbits, but only erasing the EPROM sets them.
Programming an EPROM requires a special program voltage called Vpp(25, 21 or 12.5 Volts). Parts that use a Vpp of 12.5 also require us toraise the Vcc from 5v to 6v during programming
Once the programming voltage is applied, we apply the addresslocation and data to be programmed into the EPROM. The data comes froman EPROM image in a memory buffer This Image is loaded from anotherEPROM or disk file. Then using one of the programming algorithms, weapply a programming pulse. The best deal in programmers is the pocketprogrammer.
Programming algorithms
Standard | This simplest of the algorithms, uses a set time of a 50mSprogramming pulse on each byte. After all bytes are programmed eachbyte is then verified or compared to the EPROM image in the buffer. Ifany byte does not verify then the EPROM is considered bad. |
|---|---|
Fast or intelligent | This starts with a 1mS programming pulse to program a byte.Then the byte is checked against the programming data for verification.If it does not verify, the program pulse is doubled (keeping track ofthe accumulated pulse time) and the byte is programmed again. Thisprocess is kept up until the byte is programmed. The byte is thenprogrammed again with a pulse time equal to the accumulated pulsemultiplied by 3 to be sure it sticks. If the data never verifies and the pulse is has grown to 25mS,the EPROM is bad. |
Snap! | Extreme caution must be used with this protocol. It will onlywork on the newer EPROMs. The Vpp & Vcc voltages are raised closeto the maximum levels with a Vpp of 13v & Vcc of 6.5V. Using a100uS programming pulse, the whole EPROM is programmed (similar to theStandard algorithm). Next a verification of the whole EPROM is done, ifa byte does not verify it is programmed again using a 100Us pulse untilthe byte is successfully programmed. After 10 passes withoutverification the EPROM is considered bad. On the down side it alsorequires a very high accuracy Vpp supply and is not found on manyprogrammers. (Some low end EPROM programmers have attempted thisalgorithm with disastrous results) |
32 bit | The 32 bit algorithm requires newer EPROMs of 1Meg bit orlarger (they have different internal workings). This starts by sending4 bytes of data to the EPROM that are latched internally. Then aprogramming pulse is applied which programs all 4 bytes at once. Afterall location are programmed a verification pass is done and any bytesthat do not verify are programmed again using the 8 bit Fast algorithm.The 32 bit algorithm programs large EPROMS 4 times faster, but theprogramming current is also 4 times as much and thus requires a specialVpp supply. |
Erasing an EPROM
An EPROM can only be erased using a UV light. Read and followthe safety instructions that come with EPROM erasers and light bulbs.
I have been asked:
Why do I need an EPROM eraser, can't I leave them out in the sun?
Ah, yes you can, but it can take about 3 weeks of sunny weather!.
Well then, how about a fluorescent light?
No problem, if you don't mind waiting a year or so.
Well I have a black light?
The answer is still no.
An EPROM requires a specific frequency of UV 253.7 nanometers (2537angstroms). In fact the high frequency UV light used will not passthrough plastic or most glass. To pass this light, the window in theEPROM is made of quartz crystal. The correct frequency of a lightsource alone won't guarantee proper EPROM erasure. The intensity of thelight source combined with the distance from the light sourcedetermines the intensity of the exposure. Light intensity variesinversely with the distances from the source. (The longer the distancethe lower the intensity of the light.) You will find that the closerthe chip is to the light source, the faster the EPROM will erase. Chipmanufacture tell us, 'the EPROM should be 1' from the light source withan intensity of 12mW/Cm2'. The manufactures state a 1' distance toensure that the light intensity is even over the entire EPROM, defused,with no shadows over any part of the EPROM silicon. (Yet, I havesuccessfully used a 1/2' distance to speed my prototype work.)
Besides bulb to chip distance, bulb age also effects exposure time.Be aware of the age of the EPROM technology you are erasing. Older 1.3micron technology takes longer to erase than .7 micron technology. Withall these variables, the best way to determine exposure time is to runan empirical exposure test. First, expose the EPROMs for 1 minute andtest for erasure. If they are not erased, expose them again for anotherminute. Keeping track of the total exposure time, repeat this processuntil they are erased. Now take the total time and multiply by 1.5. Forexample, if it takes 3 minutes we should use a 4.5 minutes exposuretime to ensure good erasure without over erasing. Remember if you leavean EPROM in the eraser too long, it can remain erased forever and willno longer program.
Every time an EPROM is programmed and erased it wears out a little.Erasing cycles will slow down access times, but this is usually of noconsequence unless you erase them an extreme number of cycles or for anexcessive exposure time. An EPROM with slow access time, may stillprogram and work fine on an EPROM programmer, but beware that the EPROMprogrammer does not require or test for a fast access time. A worn outEPROM may program correctly yet fail to work in the equipment thatrequires a fast access time.
Tunneling Fetch
Making Your Own Eraser? Or why not to
Germicidal light bulbs are used in hospitals for sterilizingequipment by killing germs. Germs are living cells. We are also made ofliving cells. Read and follow the safety instructions that comewith EPROM erasers and light bulbs. You are not likely to goblind from accidentally looking at the light for few seconds, butgermicidal lamps should only be operated in a safety-interlockedenclosure.
If you want to make your own eraser, you would need to get agermicidal light bulb that looks like a fluorescent lamp without thewhite coating on the inside. These are quartz tubes (remember the UVwill not pass through glass). At a light supply house you can get aG15T (a 15 Watt lamp) The ' G ' stands for germicidal the same as ' F 'stands for fluorescent (even though it has no phosphors &*???) .Just the light bulbs costs about $30.00, and you will also need a 15Watt fixture. Why not get a small ready-madeeraser for the same price? They are inexpensive, easier to use andhave built in safety interlocks.
The Difference Between C & Non-C EPROMs
The only difference between a 27256 and a 27C256 is that the 27256uses NMOS while the 27C256 uses CMOS technology. CMOS only consumesappreciable power when a signal is switching. NMOS uses N-Channel FET'swith resistor elements while CMOS avoids the power wasting resistors byusing both N and P-channel FET's. Thus CMOS avoids the production ofheat allowing tighter placements of transistors than NMOS is capableof. The high density placement of CMOS reduces the interconnect pathlengths and thus increases the speed. CMOS also shines when there islimited power such as in a battery system.
Some people have problems when programming CMOS EPROMs on olderprogrammers because of the differences in programming voltages (CMOShas a 12.5V Vpp). CMOS EPROMs also require a supply voltage (Vcc) of exactly6 Volts. CMOS parts are easier to erase but prone to die if overexposed to UV light.
Decoding EPROM Numbers
27(C)XXX are EPROMs or OTPROMSs.
Cnt Tunneling Fet
57(C)XXX are EPROMs or OTPROMSs that allow the lower 8 address linesto be multiplexed with the Data lines. (Some MCU's multiplex the loweraddress and data lines together). These parts still program like27(C)XXX EPROMs on the PocketProgrammer because the software algorithm takes this into account.
28(C)XXX are EEPROMs with the C standing for CMOS.
28FXXX are Flash EEPROMs with the F standing for Flash. Do notconfuse these with EEPROMs as they are not.
Cross list
The below parts may be the same -(according to manufactures crossguides) there may be differences including the programming algorithmused.
| Manufacturer | AMD | AMIC | Atmel | Fujitsu | Hitachi | Hynix | INTEL | Mitsu- bishi | NEC | NSC | SGS | SST | ST micro | TI | Toshiba | Winbond | PINs | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| prefix | AM | AE | ASD | AT | MBM | HN | HY | D | M5M | UPD | NM | M | SST | M | TMS | TC | W | |
| 32K | 2732 | 2732 | 2732 | 2732 | 27C32 | D2732 | 27C32Q | 2732 | 2732 | N/A | ||||||||
| 64K | 27C64 | 27C64 | 27C64 | 27C64 | 27C64 | 27C64 | 27C64Q | 27C64 | 27C64 | N/A | ||||||||
| 128K | 27C128 | 27C128 | 27C128 | 27C128 | 27C128 | 27C128 | 27C128Q | 27C128 | 27C128 | N/A | ||||||||
| 256K | 27C256 | 27C256 | 27C256 | 27C256 | 27C256 | 27C256 | 27C256 | 27C256Q | 27C256 | 27SF256 | 27256 | 27C256 | 57256 | |||||
| 28HC256 | ||||||||||||||||||
| 512K | 27C512 | 27C512 | 27C512 | 27C512 | 27C512 | 27C512 | 27C512 | 27C512Q | 27C512 | 27SF512 | 27C512 | 27C512 | 57512 | 27E512 | ||||
| 28F512 | 29C512 | 29EE512 | ||||||||||||||||
| 49C512 | 39SF512 | 29F512 | 29EE512 | |||||||||||||||
| 1MEG | 27C010 | 29010 29001 290011 | 29F1008 | 27C010 | 27C1001 | 27C010 | 27C010 | 27C101 | 27C1001 | 27C010Q | 27C1001 | 27SF010 | 27C1001 | 27C010 | 571000 | 27E010 | ||
| 29C010 | ||||||||||||||||||
49F001 | 28F001 | 39SF010 | 29F010 | 29EE011 | ||||||||||||||
| 28F010 | 49F010 | 28F010 | ||||||||||||||||
| 29C010 | 29EE010 | |||||||||||||||||
| 2MEG | 27C020 | 29F2008 | 27C020 | 27C2001 | 27C020 | 27C020 | 27C201 | 27C2001 | 27C020Q | 27C2001 | 27SF020 | 27C2001 | 27C020 | N/A | 27E020 | |||
| 29F002 | 29C020 49F020 49F002 | 29F002 | 28F002 | 29EE020 39SF020 | 29F002 | 29C020 | ||||||||||||
| 4MEG | 27C040 | 27C4001 | 27C040 | 27C040 | 27C401 | 27C4001 | 27C040Q | 27C4001 | 27C040 | 574000 | ||||||||
| 29F040 | 29C040 49F040 | 28F004 | 28SF040 39SF040 | 28SF040 29F040 | 29040 | |||||||||||||
| 29F040 | 29F040 | 29F040 | 29F040 | BM29F040 | ||||||||||||||
| x16 | 29F400 | 29F400 | 29F400 | |||||||||||||||
| 8MEG | 27C801 | 32 | ||||||||||||||||
| 29F080 | 29F080 | 29F080 | ||||||||||||||||
| x16 | 29F800 | 29F800 | 29F800 | |||||||||||||||
| 16MEG | 29002 290021 | 32 | ||||||||||||||||
| 32MEG | 29400 29040A | 32/48 | ||||||||||||||||
| 64Meg | 29800 | 48 |
Disclaimer
This information may have errors; It is not permissible to be read byanyone who has ever met a lawyer.Band To Band Tunneling
Use is confined to Engineers with more than 370 course hours ofelectronic engineering for theoretical studies.ph +1(785) 841-3089 Emailinform@xtronics.com
Tunneling Fett
(C) Copyright 1994-2017, Transtronics, Inc. All rightsreserved
Transtronics® is a registered trademark of Transtronics, Inc.
All trademarks are the property of their respective owners.
